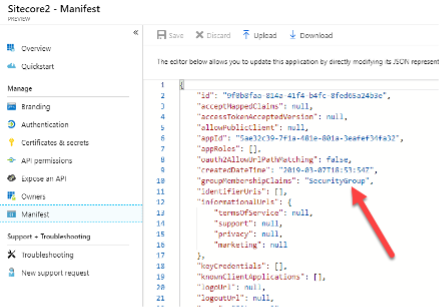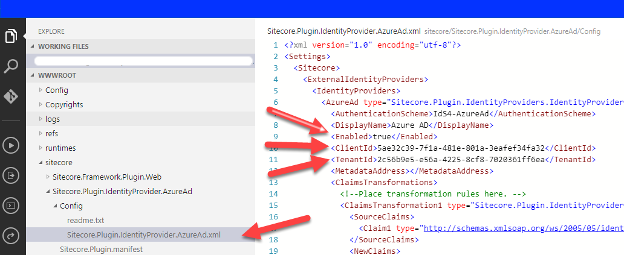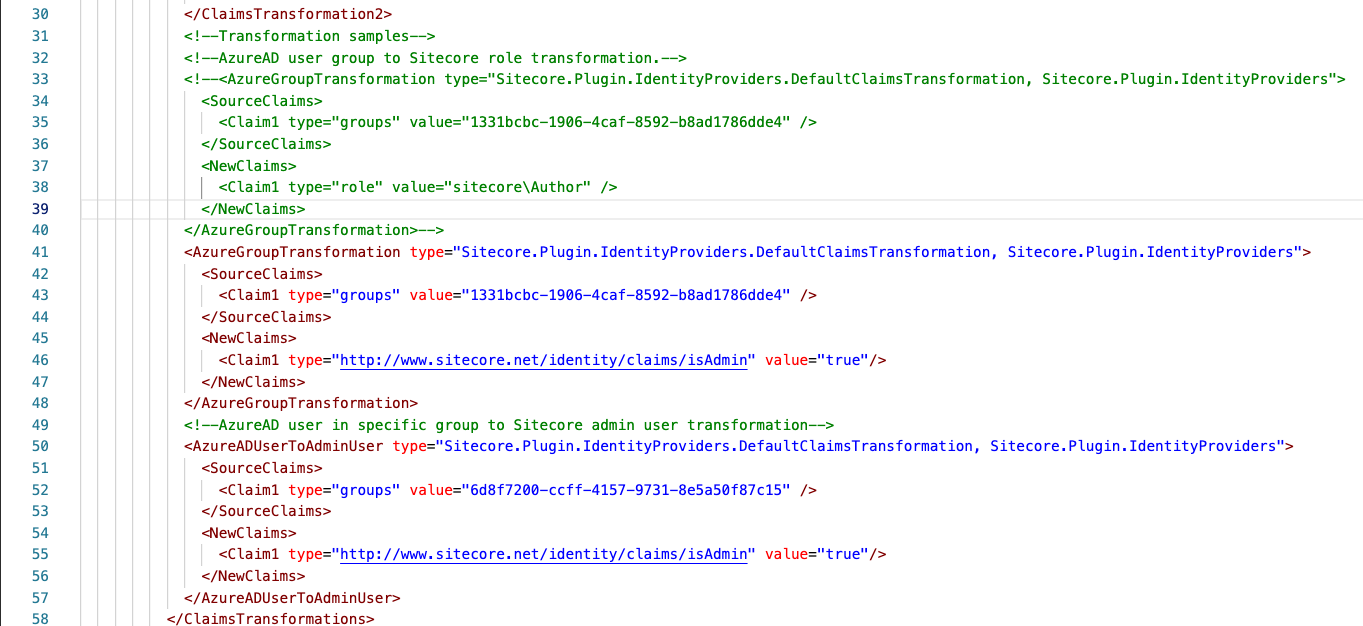
Welcome to the first installment of this series, where I share key insights gained from migrating Sitecore across versions. Whether transitioning from on-premises to Azure, migrating workloads from AWS to Azure, or navigating complex upgrades, this series is designed to equip Sitecore customers with the knowledge and strategies needed for seamless execution.
Throughout this guide, we’ll explore critical considerations, feature priorities, and best practices for ensuring a smooth transition between environments. Stay tuned for expert insights that will help you optimize your Sitecore upgrade journey.
Overview of Sitecore 10.0: There are lot of Blogs to detail this aspects. I would like to indicate that Sitecore has been very good with the Change Logs so you can keep watching and reading more from time to time from the real source.
Why Upgrade?
Upgrading to latest versions of Sitecore is not just a recommendation; it’s a strategic necessity. With Sitecore having declared end-of-support for lower versions, continuing to use outdated versions can expose your organization to security vulnerabilities and lack of technical support. Customers have reported increasing difficulties in managing and maintaining integrations with third-party products, which can hinder operational efficiency and innovation.
Moreover, the build and development paradigm has evolved significantly. Sitecore introduces modern development practices and tools that streamline workflows, enhance performance, and improve scalability. By upgrading, you ensure that your platform remains robust, secure, and capable of leveraging the latest features and integrations, ultimately providing a better experience for both your team and your end-users.
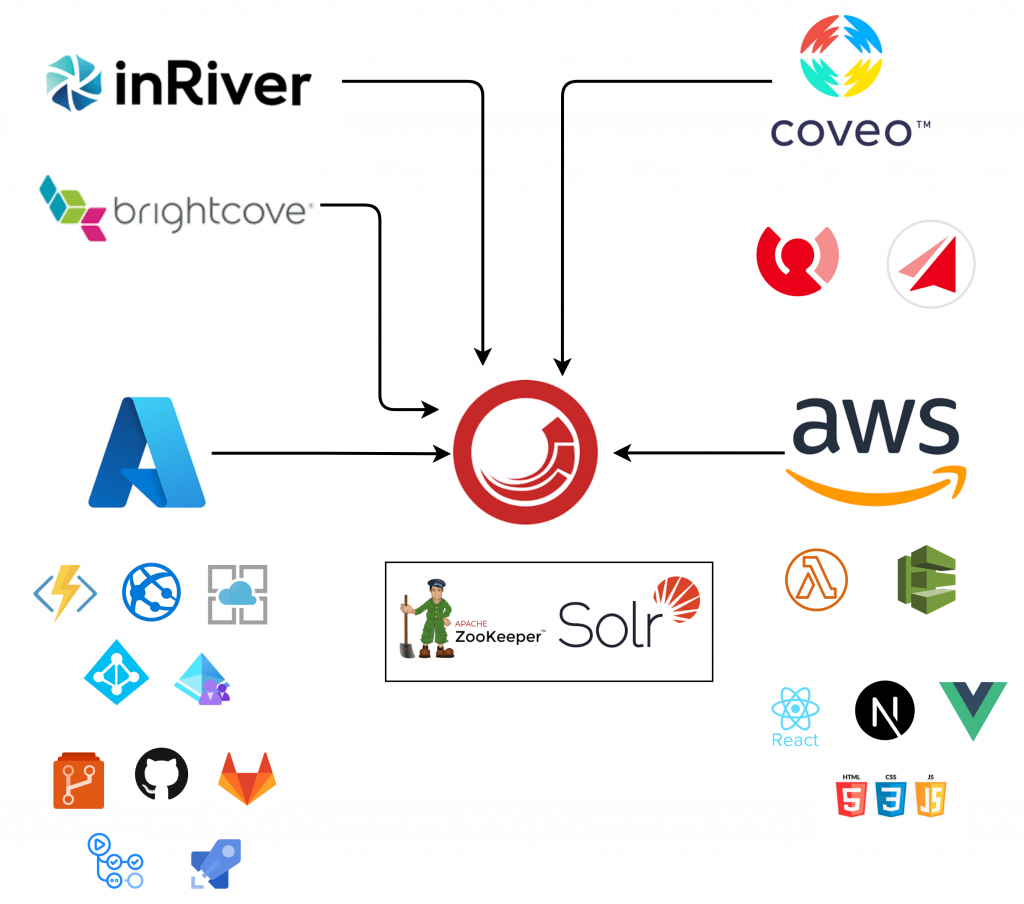
One other way is to avoid code bloat, and also prepare to Move towards PaaS and SaaS from IaaS and or on-premises.
Preparation Steps: Before starting the upgrade, it’s essential to:
- Assess Current Environment: Understand your current setup and identify any customizations or integrations.
- Backup Data: Ensure all data is backed up to prevent any loss during the upgrade.
- Review Documentation: Familiarize yourself with the official Sitecore upgrade documentation and guidelines.
Initial Setup: Begin the upgrade process by:
- Setting Up a Test Environment: Create a staging environment to test the upgrade without affecting the live site.
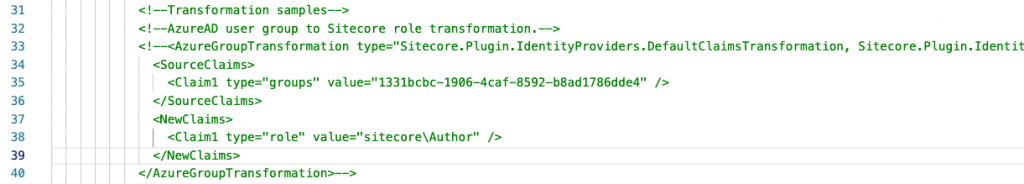
- Running Compatibility Checks: Ensure all modules and customizations are compatible with Sitecore, Sitecore Forms, Custom Components, Compatibility with SXA Modules are few of them to note.
- Planning Downtime: Schedule the upgrade during a period of low traffic to minimize disruption.
Conclusion: Upgrading Sitecore is a strategic move that requires careful planning and execution. In the next post, we’ll dive into the detailed steps for upgrading to Sitecore 10.4, addressing common challenges and providing solutions.
Stay Tuned: Follow along as we guide you through each step of the upgrade process, ensuring a smooth transition and optimal performance.